Monitoring for phishing pages is something we are working on as part of the intelligence ingestion for our platform, and manually digging into cases is often beneficial to better understand what it is we are looking for.
Recently while monitoring for suspicious SSL/TLS certificates being issued (using CertStream), we came across a NatWest phishing site that had just been deployed. It was impersonating NatWest’s “Personal Banking” login page, and takes the victim through a number of steps in order to steal their personal information.
We will walk you through the scam below with screenshots of each step, to show you how it works.
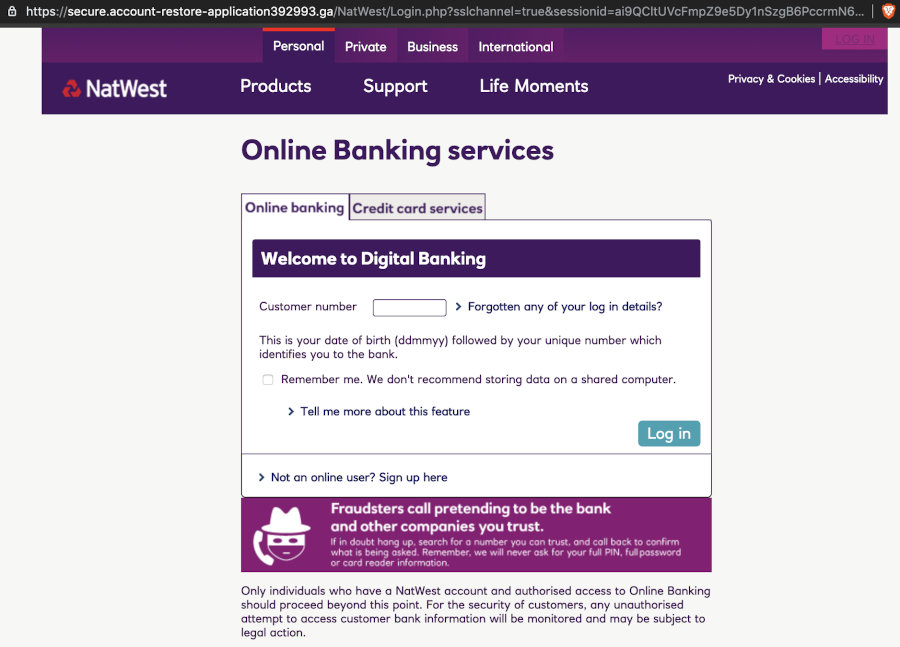
On the first page, as shown above, you are presented with the digital banking login page, asking for your customer number. It helpfully tells you what format the number is in, and even contains a fraud warning!
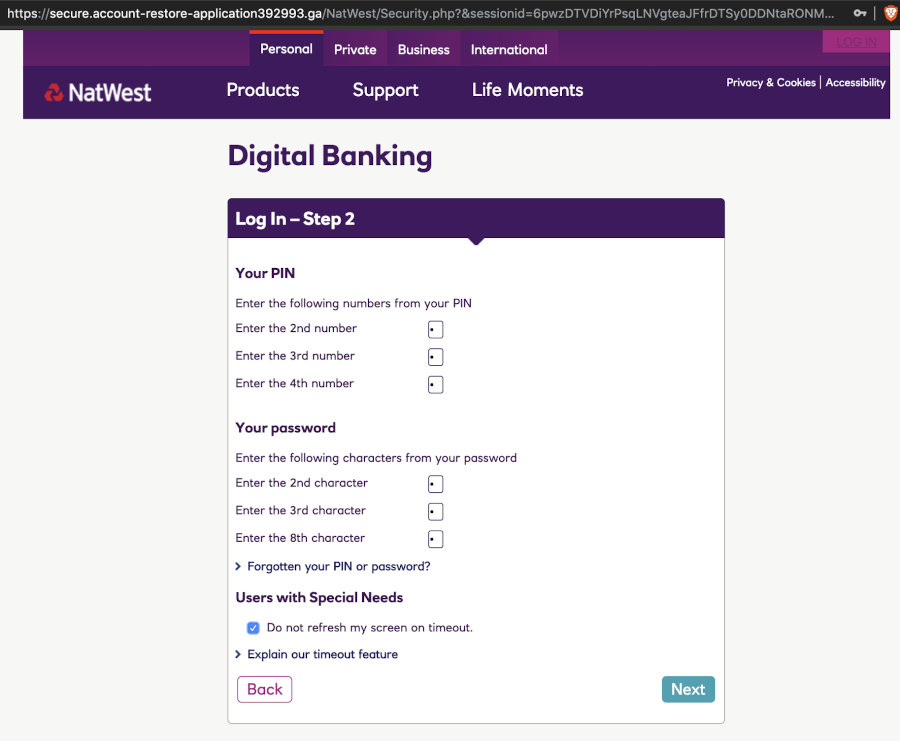
After you provide your “customer number”, you are presented with one of these godawful screens banks like to use, asking for parts of your PIN and password. Banks do this apparently to defeat keyloggers, but it is effectively useless and also hints at them storing authentication credentials in cleartext, or some recoverable/comparable format. We enter some random nonsense and carry on.
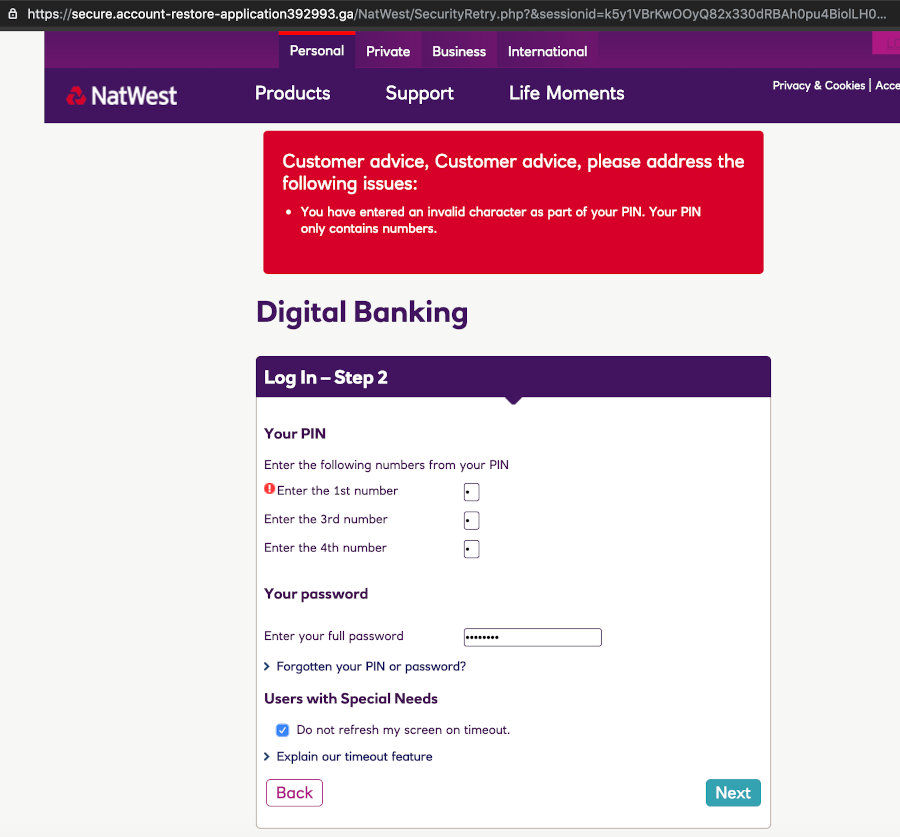
This next part is quite clever - it pitches an “error”, and asks for “some parts of your PIN” again. Note that this time it asks for the 1st, 3rd, and 4th, while the previous screen asked for the 2nd, 3rd and 4th. The attacker now has your full PIN.
They also request your full password on this screen. Throwing an error will usually distract the user just enough to make them not think too hard about this.
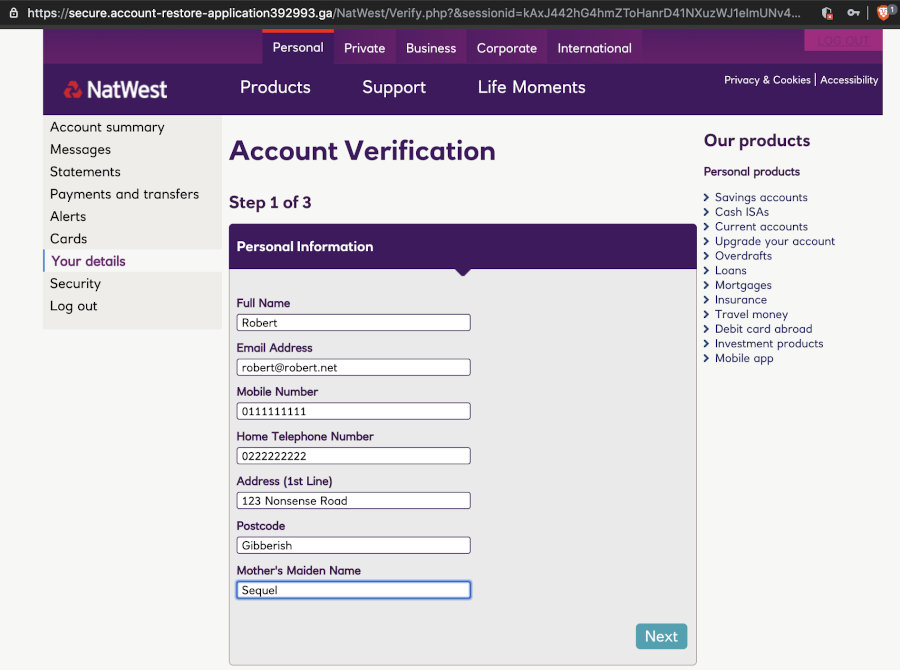
We get sent to another screen now, which asks for further details for “account verification purposes”. All of the information they are requesting is very, very useful to an identity thief.
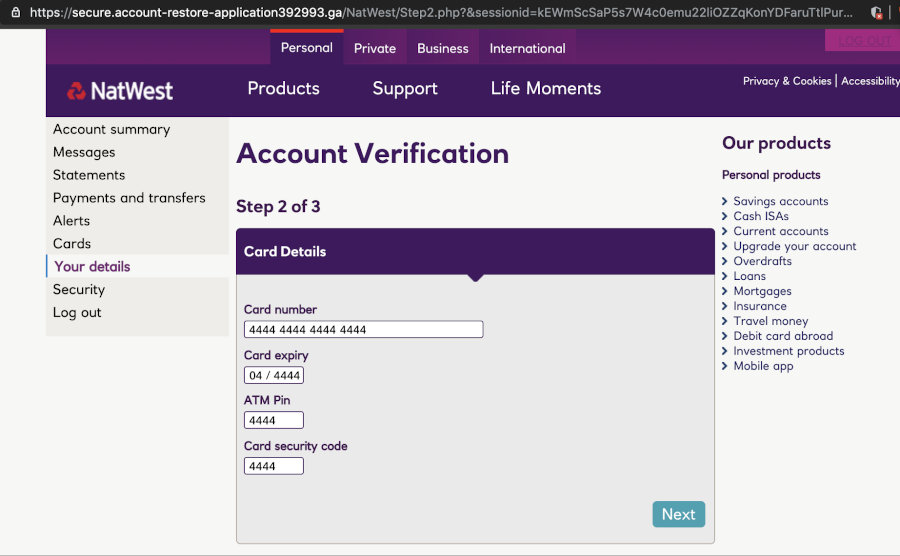
To continue verifying our account, we are asked to give the “bank” our card number and other card details, for, uhhh, verification. Users unversed in phishing will figure “the bank has this already, its fine” and hand over the information readily. After all, they need to get into their bank account!
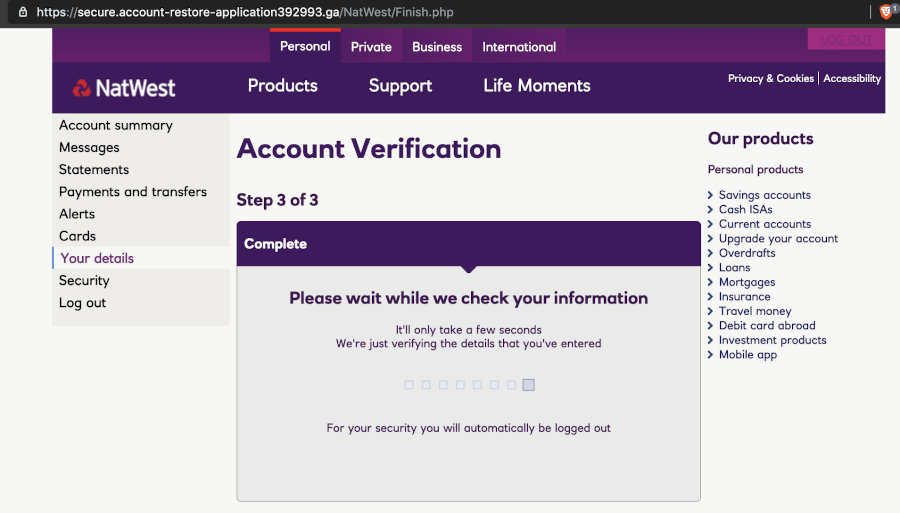
Now we land on this “Checking” page, which does nothing. It just waits a few seconds and then bounces us to the legitimate Natwest website.
So now that we have walked you through the “user flow” of the scam, lets extract some information from this phishing site. We begin by traversing up a directory, in the hopes that they left something behind… And we strike gold, as seen below.
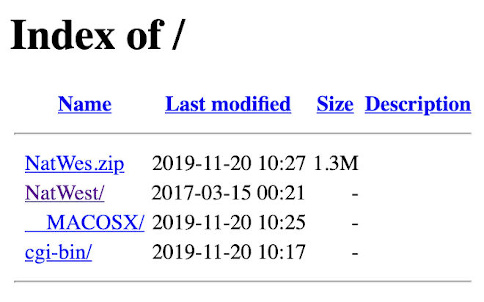
In this directory, we notice that the attackers left behind a zip file containing probably the source code of the phishing site. We grab a copy of the zip file to take apart locally to understand how this scam works.
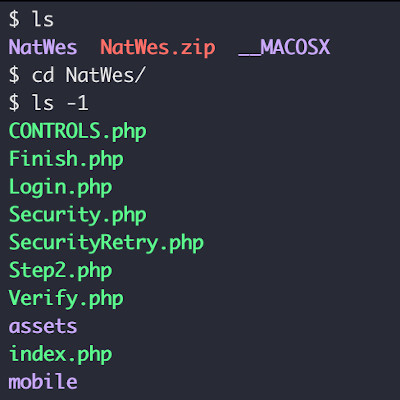
Upon unpacking the zip file, we find it contains a number of PHP scripts, along with images, fonts, and JS assets. We decided a good place to start would be the PHP scripts.
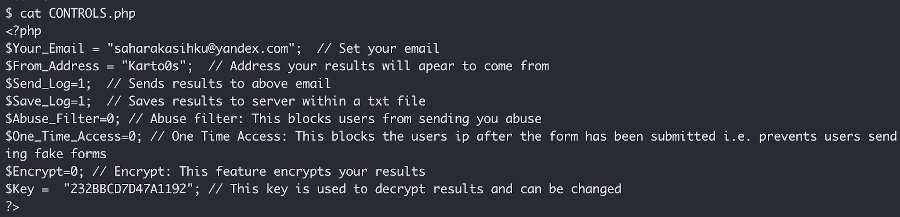
In this PHP script, the configuration settings are to be found, including the email address that the stolen data is to be exfiltrated to, whether or not to encrypt the data being sent, and the encryption key for the stolen data. In this case, the attacker chose not to encrypt the stolen data.
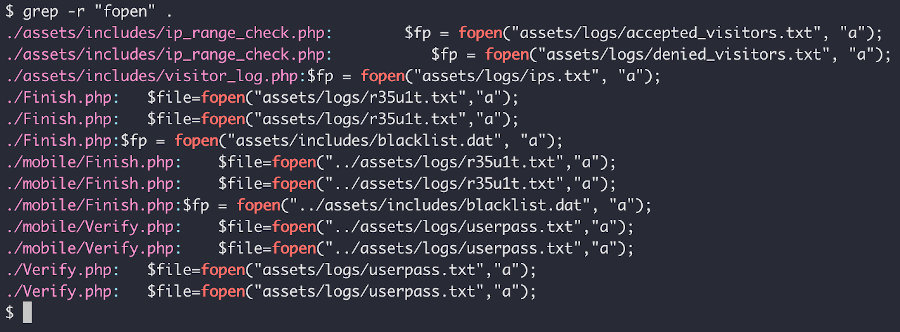
A quick grep for “fopen” shows that the kit not only exfils via email but, as hinted by the config file, stores logs locally on the web server. We decided to have a quick look and see if the logs were web accessible.
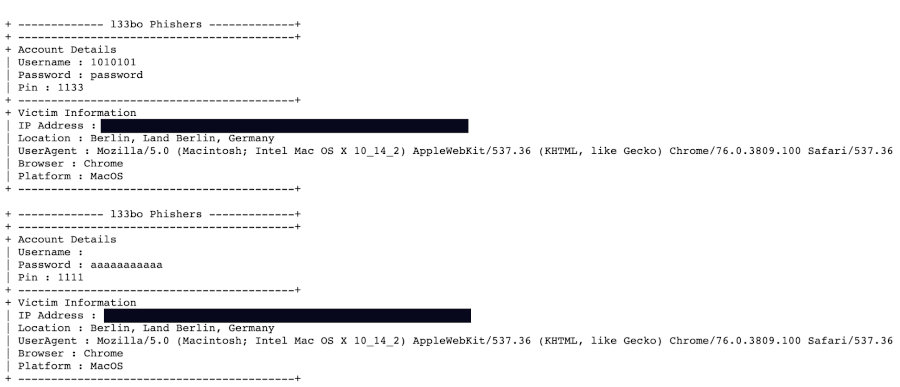
TL;DR: they were. In this screenshot you can see the junk data we entered. Any other attacker aware of this could “scavenge” results from these guys phishing operation.
In conclusion, we were able to rapidly identify an active phishing campaign before it had even received any clicks from “real victims”, extracting a wealth of information from it by identifying a deployment failure on behalf of the threat actor.
While this actor was not the most sophisticated, and the kit itself was clearly cobbled together using copy-paste programming, the risks posed by these adversaries are very real, as is the distress caused to their victims.
We will be writing up more of these in the future, as we work on improving our processes in order to automate a whole bunch of the “work” being performed.

